Argo CD 是什么
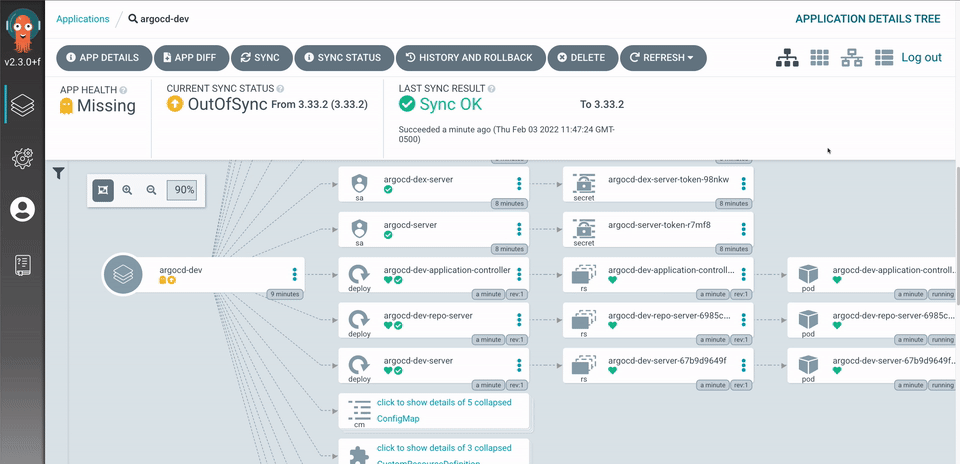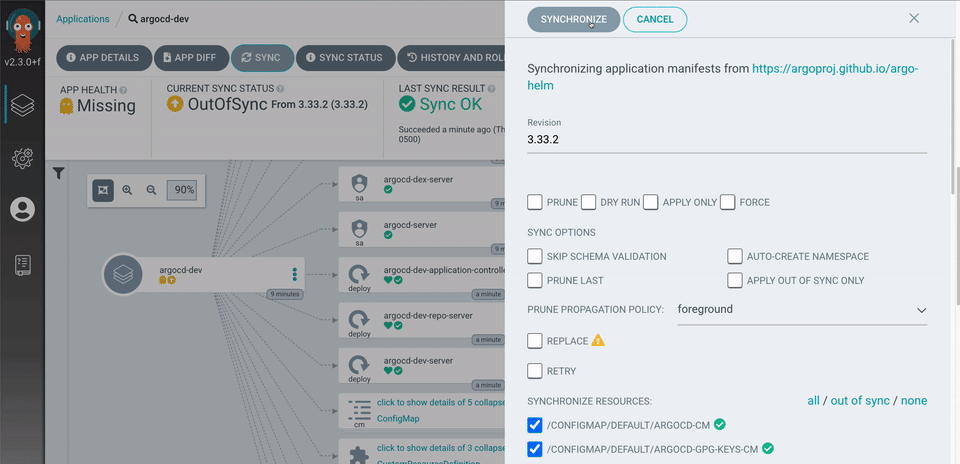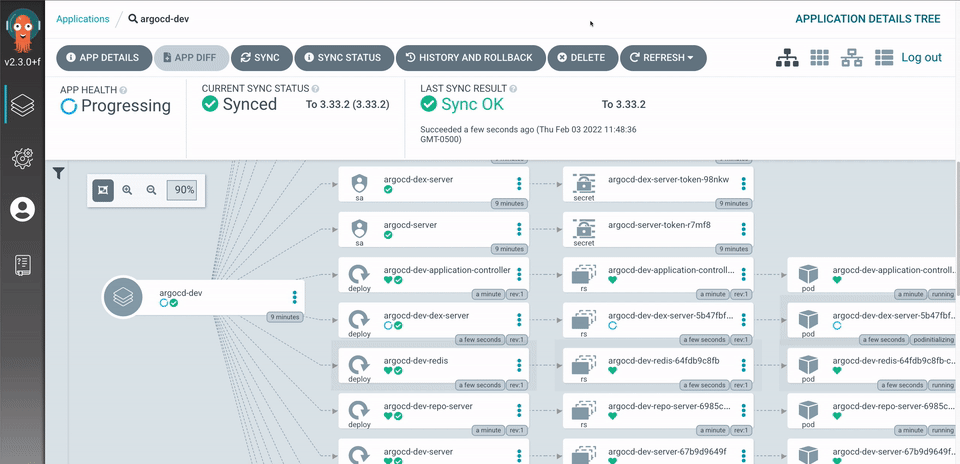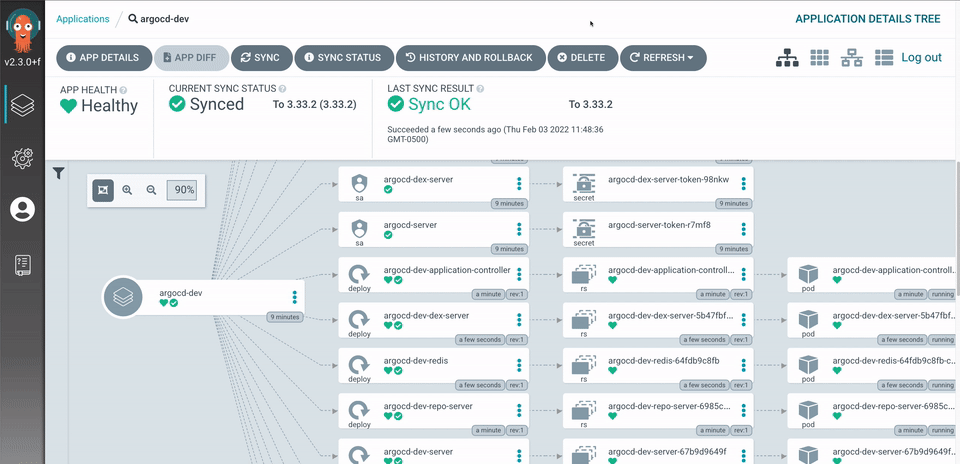
Argo CD 是一款针对 Kubernetes 的开源 GitOps Operator,它是 Argo 家族中的一员。Argo CD 专注于应用程序交付的使用场景。
Argo CD 提供了一个用户友好的 Web 界面。使用 Web 界面,你可以获得跨多个集群部署的所用应用程序的高级视图,以及有关每个应用程序资源非常详细的信息。
Argo CD不直接使用任何数据库(Redis被用作缓存),所以它看起来没有任何状态。
Argo CD 可以理解为一个 Kubernetes 控制器,它会持续监控正在运行的应用,并将当前的实际状态与 Git 仓库中声明的期望状态进行比较,如果实际状态不符合期望状态,就会更新应用的实际状态以匹配期望状态。Argo CD是一个持续交付(CD)工具,而持续集成(CI)部分可以由 Jenkins,Gitlab Runner来完成。
Argo CD官方文档地址
https://argo-cd.readthedocs.io/en/stable/
Argo CD 架构
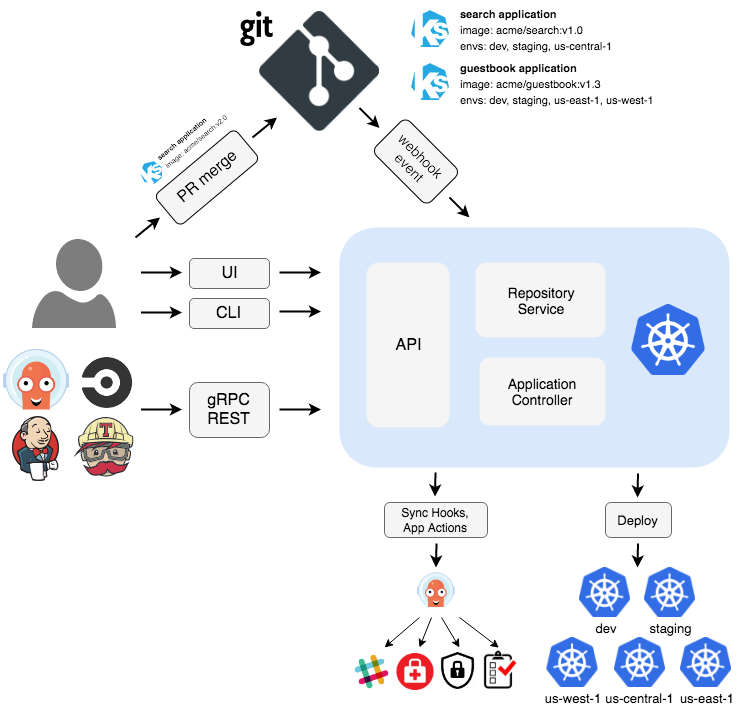
分离配置库和源代码库
使用单独的Git存储库来保存kubernetes清单,将配置与应用程序源代码分开,强烈推荐使用,原因如下:
- 清晰分离了应用程序代码与应用程序配置。有时您希望只修改清单,而不触发整个CI构建。
例如,如果您只是希望增加部署规范中的副本数量,那么您可能不希望触发构建(由于构建周期可能较长) - 更清洁的审计日志。出于审计目的,只保存配置库历史更改记录,而不是掺有日常开发提交的日志记录。
- 微服务场景下,应用程序可能由多个Git库构建的服务组成,但是作为单个单元部署(比如同一pod内)。
通常,微服务应用由不同版本和不同发布周期的服务组成(如ELK, Kafka + Zookeeper)。
将配置清单存储在单个组件的一个源代码库中可能没有意义 - 访问的分离。开发应用程序的开发人员不一定是能够/应该推送到生产环境的同一个人,无论是有意的还是无意的。
通过使用单独的库,可以将提交访问权限授予源代码库,而不是应用程序配置库 - 自动化CI Pipeline场景下,将清单更改推送到同一个Git存储库可能会触发构建作业和Git提交触发器的无限循环。
使用一个单独的repo来推送配置更改,可以防止这种情况发生。
git设置分支命名参考
- master (main) 线上主分支,永远是可用的稳定版本
- develop 默认,开发主分支
- prerelease (staging) 预发布分支
- release/*分支(发布分支,短期从develop创建,主要用于测试和版本发布)
临时性分支
- feature-xxx (功能开发分支,在develop上创建分支,以自己开发功能模块命名,功能测试正常后合并到develop分支)
- feature-xxx-fix(功能bug修复分支,feature分支合并之后发现bug,在develop上创建分支进行修复,之后合并回develop分支)
- hotfix-xxx(紧急bug修改分支,在master分支上创建,修复完成后合并到master)
- bugfix/*分支 (短期从develop创建)
- backup (备份分支)
gitlab 配制argocd 拉取 token
connect repo
需要注意的是这里的密码需要使用 AccessToken,我们可以前往 GitLab 的页面 http://gitlab.k8s.local/-/profile/personal_access_tokens 创建。
git->settings->Access Tokens
api
read_api
read_repository
产生token
-4m8nyfa4SvLtEsxVFzU
Argocd触发CD
Argo CD每三分钟轮询一次Git存储库,以检测清单的变化。如果Applications设置为Auto Sync,那么会重新部署。
同时Argo CD也支持接收Webhook事件,可以消除轮询带来的延迟.
Argo CD Image Updater
根据镜像仓库的镜像 Tag 变化,完成服务镜像更新。
目前,它仅适用于使用Kustomize或Helm工具构建的应用程序。 尚不支持从纯 YAML 或自定义工具构建的应用程序。
在 ArgoCD 中启动/停止应用程序
首先禁用自动同步
您需要编辑部署的定义,将其设置replicas为0如下所示:
apiVersion: ...
kind: Deployment
spec:
replicas: 0
...如果删除applications,那么有状态服务如mysql使用StorageClass会重新绑一个pvc.和 kubectl delete -f . 的操作不同
argocd安装
- 方式一 Helm
- 方式二 使用 红帽 operator 的方式部署 ArgoCD
- 方式三 使用 argo-cd github operator
方式一 Helm
https://artifacthub.io/packages/helm/argo/argo-cd
cd /root/k8s/helm
helm repo add argo https://argoproj.github.io/argo-helm
helm pull argo/argo
helm install my-argo-cd argo/argo-cd –version 6.7.7
方式二 使用 红帽 operator 的方式部署 ArgoCD
官网地址: https://operatorhub.io/operator/argocd-operator
安装 OLM 组件
curl -sL https://github.com/operator-framework/operator-lifecycle-manager/releases/download/v0.26.0/install.sh | bash -s v0.26.0
kubectl create -f https://operatorhub.io/install/argocd-operator.yaml
kubectl get csv -n operators
https://github.com/operator-framework/operator-lifecycle-manager/releases/download/v0.26.0/crds.yaml
https://github.com/operator-framework/operator-lifecycle-manager/releases/download/v0.26.0/olm.yaml
operatorhub.io网络太慢,无法安装,放弃,改用github https://github.com/argoproj/argo-cd
方式三 argo-cd github operator
参考: https://blog.csdn.net/engchina/article/details/129611785
在 K8S 中部署 ArgoCD
单机版Non-HA:
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/v2.9.2/manifests/install.yaml
高可用HA:
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/v2.9.2/manifests/ha/install.yaml
单机版Non-HA安装
这里安装单机版 Non-HA,如果是生产,那么建议使用ha版本
wget –no-check-certificate https://raw.githubusercontent.com/argoproj/argo-cd/v2.9.2/manifests/install.yaml -O argo-cd-v2.9.2.yaml
wget –no-check-certificate https://raw.githubusercontent.com/argoproj/argo-cd/v2.10.0/manifests/install.yaml -O argo-cd-v2.10.0.yaml
准备image
将镜像拉取到harbor私仓,方便以后重复使用 ,没有私仓则跳过此步骤。
cat argo-cd-v2.9.2.yaml|grep image:|sed -e ‘s/.*image: //’|sort|uniq
ghcr.io/dexidp/dex:v2.37.0
quay.io/argoproj/argocd:v2.9.2
redis:7.0.11-alpine
docker pull quay.io/argoproj/argocd:v2.9.2
docker pull redis:7.0.11-alpine
docker pull ghcr.io/dexidp/dex:v2.37.0
#docker pull quay.nju.edu.cn/argoproj/argocd:v2.9.2 #加速地址 426MB
docker tag quay.nju.edu.cn/argoproj/argocd:v2.9.2 repo.k8s.local/quay.io/argoproj/argocd:v2.9.2
docker tag redis:7.0.11-alpine repo.k8s.local/docker.io/redis:7.0.11-alpine
docker tag ghcr.io/dexidp/dex:v2.37.0 repo.k8s.local/ghcr.io/dexidp/dex:v2.37.0
docker push repo.k8s.local/quay.io/argoproj/argocd:v2.9.2
docker push repo.k8s.local/docker.io/redis:7.0.11-alpine
docker push repo.k8s.local/ghcr.io/dexidp/dex:v2.37.0
docker rmi quay.nju.edu.cn/argoproj/argocd:v2.9.2
docker rmi redis:7.0.11-alpine
docker rmi ghcr.io/dexidp/dex:v2.37.0cat argo-cd-v2.10.0.yaml|grep image:|sed -e ‘s/.*image: //’|sort|uniq
ghcr.io/dexidp/dex:v2.37.0
quay.io/argoproj/argocd:v2.10.0
redis:7.0.14-alpine
#docker pull quay.nju.edu.cn/argoproj/argocd:v2.10.0 #加速地址 426MB
docker pull argoproj/argocd:v2.10.0
docker pull redis:7.0.14-alpine
docker pull ghcr.io/dexidp/dex:v2.37.0
docker tag quay.nju.edu.cn/argoproj/argocd:v2.10.2 repo.k8s.local/quay.io/argoproj/argocd:v2.10.2
docker tag docker.io/library/redis:7.0.14-alpine repo.k8s.local/docker.io/library/redis:7.0.14-alpine
docker tag ghcr.io/dexidp/dex:v2.37.0 repo.k8s.local/ghcr.io/dexidp/dex:v2.37.0
docker push repo.k8s.local/quay.io/argoproj/argocd:v2.10.2
docker push repo.k8s.local/docker.io/redis:7.0.14-alpine
docker push repo.k8s.local/ghcr.io/dexidp/dex:v2.37.0
docker rmi quay.nju.edu.cn/argoproj/argocd:v2.10.2
docker rmi redis:7.0.14-alpine
docker rmi ghcr.io/dexidp/dex:v2.37.0
替换yaml中image地址为私仓
没有私仓则跳过此步骤,也可替换为其它镜像源。
#测试
sed -n "/image:/{s/image: redis/image: repo.k8s.local\/docker.io\/redis/p}" argo-cd-v2.9.2.yaml
sed -n "/image:/{s/image: ghcr.io/image: repo.k8s.local\/ghcr.io/p}" argo-cd-v2.9.2.yaml
sed -n "/image:/{s/image: quay.io/image: repo.k8s.local\/quay.io/p}" argo-cd-v2.9.2.yaml
#替换
sed -i "/image:/{s/image: redis/image: repo.k8s.local\/docker.io\/redis/}" argo-cd-v2.9.2.yaml
sed -i "/image:/{s/image: ghcr.io/image: repo.k8s.local\/ghcr.io/}" argo-cd-v2.9.2.yaml
sed -i "/image:/{s/image: quay.io/image: repo.k8s.local\/quay.io/}" argo-cd-v2.9.2.yaml
#重新验证
cat argo-cd-v2.9.2.yaml|grep image:|sed -e 's/.*image: //'先创建argocd 命名空间,再部署argocd服务
kubectl create namespace argocd
kubectl apply -n argocd -f argo-cd-v2.9.2.yaml
argocd-application-controller: controller 是argocd的处理器,主要是帮你管理你的k8s 资源,基本上你之前用kubectl 做的的操作它都集成了,operater的controller。
argocd-dex-server: 认证token服务,为后面实现gitlab登录等。高可用版本时候不支持多pod,只能单个pod。
argocd-redis: 缓存所用。
argocd-repo-server: 这个服务主要功能是去git 你的gitlab 公有/私有仓库到argocd-repo-server这个pod里面最后让argocd进行相应的kubectl 操作。高可用建议:多个pod来处理多个应用在一个repo的场景。repo管理建议:repo里面主要存放配置管理文件以免消耗过多的本地空间,因为argocd-repo-server会拉取你的repo 到本地。如果repo实在是太大的话,建议挂载磁盘到该服务的/tmp目录。
argocd-server: argocd 的前后端服务,整个web服务。里面还内置helm/kubectl 等工具,具体可以进入到pod里面去查看。
kubectl get pods -n argocd
NAME READY STATUS RESTARTS AGE
argocd-application-controller-0 1/1 Running 0 20m
argocd-applicationset-controller-5b5f95888b-lwfjd 1/1 Running 0 20m
argocd-dex-server-cb9f4d4b-4vgmc 1/1 Running 0 20m
argocd-notifications-controller-5c6d9d776f-4hfdw 1/1 Running 0 20m
argocd-redis-6b68b8b86d-62jv8 1/1 Running 0 20m
argocd-repo-server-67855f9d8c-995c8 1/1 Running 0 20m
argocd-server-7bcff8887b-qfnb2 1/1 Running 0 20m
kubectl -n argocd describe pod/argocd-dex-server-f7648d898-fgklf
kubectl -n argocd logs pod/argocd-dex-server-f7648d898-fgklf 下载安装Argo CD CLI
方式一
VERSION=$(curl --silent "https://api.github.com/repos/argoproj/argo-cd/releases/latest" | grep '"tag_name"' | sed -E 's/.*"([^"]+)".*/\1/')
curl -sSL -o /usr/local/bin/argocd https://github.com/argoproj/argo-cd/releases/download/$VERSION/argocd-linux-amd64
chmod +x /usr/local/bin/argocd方式二
curl -sSL -o argocd-linux-amd64 https://github.com/argoproj/argo-cd/releases/latest/download/argocd-linux-amd64
sudo install -m 555 argocd-linux-amd64 /usr/local/bin/argocd
rm argocd-linux-amd64
argocd version
argocd: v2.9.2+c5ea5c4
BuildDate: 2023-11-20T17:37:53Z
GitCommit: c5ea5c4df52943a6fff6c0be181fde5358970304
GitTreeState: clean
GoVersion: go1.21.4
Compiler: gc
Platform: linux/amd64
FATA[0000] Argo CD server address unspecified 配置ingress 访问Argo CD web页面
ingress配置文档地址: https://argo-cd.readthedocs.io/en/stable/operator-manual/ingress/
Argo CD 在同一端口 (443) 上提供多个协议 (gRPC/HTTPS),所以当我们为 argocd 服务定义单个 nginx ingress 对象和规则的时候有点麻烦,因为 nginx.ingress.kubernetes.io/backend -protocol 这个 annotation 只能接受一个后端协议(例如 HTTP、HTTPS、GRPC、GRPCS)。
为了使用单个 ingress 规则和主机名来暴露 Argo CD APIServer,必须使用 nginx.ingress.kubernetes.io/ssl-passthrough 这个 annotation 来传递 TLS 连接并校验 Argo CD APIServer 上的 TLS。
除此之外,由于 ingress-nginx 的每个 Ingress 对象仅支持一个协议,因此另一种方法是定义两个 Ingress 对象。一个用于 HTTP/HTTPS,另一个用于 gRPC
cat > argocd-ingress.yaml <<EOF
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: argocd-server-ingress
namespace: argocd
labels:
app.kubernetes.io/name: nginx-ingress
app.kubernetes.io/part-of: argocd
annotations:
cert-manager.io/cluster-issuer: letsencrypt-prod
nginx.ingress.kubernetes.io/force-ssl-redirect: "true"
nginx.ingress.kubernetes.io/ssl-passthrough: "true"
# If you encounter a redirect loop or are getting a 307 response code
# then you need to force the nginx ingress to connect to the backend using HTTPS.
#
nginx.ingress.kubernetes.io/backend-protocol: "HTTPS"
spec:
ingressClassName: int-ingress-nginx
rules:
- host: argocd.k8s.local
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: argocd-server
port:
name: https
tls:
- hosts:
- argocd.k8s.local
secretName: argocd-server-tls # as expected by argocd-server
EOF在Ingress配置文档中可以找到上面的yaml文件内容,创建ingress的yaml文件,Argocd是https访问模式,其中的访问证书tls secret Argo CD已经提供,我们不需要改变,我们只需要改一下hosts并 配置域名就可以。hosts是我自己的,大家需要改成自己喜欢的域名
kubectl delete -f argocd-ingress.yaml
kubectl apply -f argocd-ingress.yaml
kubectl get svc -n argocd
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
argocd-applicationset-controller ClusterIP 10.96.248.76 <none> 7000/TCP,8080/TCP 49m
argocd-dex-server ClusterIP 10.96.159.94 <none> 5556/TCP,5557/TCP,5558/TCP 49m
argocd-metrics ClusterIP 10.96.31.187 <none> 8082/TCP 49m
argocd-notifications-controller-metrics ClusterIP 10.96.199.238 <none> 9001/TCP 49m
argocd-redis ClusterIP 10.96.94.14 <none> 6379/TCP 49m
argocd-repo-server ClusterIP 10.96.255.97 <none> 8081/TCP,8084/TCP 49m
argocd-server ClusterIP 10.96.10.228 <none> 80/TCP,443/TCP 49m
argocd-server-metrics ClusterIP 10.96.117.128 <none> 8083/TCP 49m
kubectl get ingress -n argocd
NAME CLASS HOSTS ADDRESS PORTS AGE
argocd-server-ingress nginx argocd.k8s.local localhost 80, 443 57scurl -k -H "Host:argocd.k8s.local" http://10.96.10.228:80/
curl -k -H "Host:argocd.k8s.local" https://10.96.10.228:443/
curl -k -H "Host:argocd.k8s.local" http://192.168.244.7:80/
<html>
<head><title>308 Permanent Redirect</title></head>
<body>
<center><h1>308 Permanent Redirect</h1></center>
<hr><center>nginx</center>
</body>
</html>
curl -k -H "Host:argocd.k8s.local" https://192.168.244.7:443/
<!doctype html><html lang="en"><head><meta charset="UTF-8"><title>Argo CD</title><base href="/"><meta name="viewport" content="width=device-width,initial-scale=1"><link rel="icon" type="image/png" href="assets/favicon/favicon-32x32.png" sizes="32x32"/><link rel="icon" type="image/png" href="assets/favicon/favicon-16x16.png" sizes="16x16"/><link href="assets/fonts.css" rel="stylesheet"><script defer="defer" src="main.9a9248cc50f345c063e3.js"></script></head><body><noscript><p>Your browser does not support JavaScript. Please enable JavaScript to view the site. Alternatively, Argo CD can be used with the <a href="https://argoproj.github.io/argo-cd/cli_installation/">Argo CD CLI</a>.</p></noscript><div id="app"></div></body><script defer="defer" src="extensions.js"></script></html>登录Argo CD web页面
用户名是 admin ,初始密码在名为 argocd-initial-admin-secret 的 Secret 对象下的 password 字段中可以用一下命令获取
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d
peWrTVUl6d0ivUg9
#也可以通过以下命令来修改登录密码:
$ argocd account update-password --account admin --current-password xxxx --new-password xxxx
argocd account update-password --account admin --current-password peWrTVUl6d0ivUg9- --new-password c1gstudio输入的Ip地址就是argocd-server的ClusterIP 可以通过命令查询
kubectl get svc -n argocd |grep argocd-server
也可以使用Argo CD CLI 登录
argocd login 10.96.10.228
WARNING: server certificate had error: tls: failed to verify certificate: x509: cannot validate certificate for 10.96.10.228 because it doesn't contain any IP SANs. Proceed insecurely (y/n)? y
Username: admin
Password:
'admin:login' logged in successfully
Context '10.96.10.228' updated
argocd version
argocd: v2.9.2+c5ea5c4
BuildDate: 2023-11-20T17:37:53Z
GitCommit: c5ea5c4df52943a6fff6c0be181fde5358970304
GitTreeState: clean
GoVersion: go1.21.4
Compiler: gc
Platform: linux/amd64
argocd-server: v2.9.2+c5ea5c4
BuildDate: 2023-11-20T17:18:26Z
GitCommit: c5ea5c4df52943a6fff6c0be181fde5358970304
GitTreeState: clean
GoVersion: go1.21.3
Compiler: gc
Platform: linux/amd64
Kustomize Version: v5.2.1 2023-10-19T20:13:51Z
Helm Version: v3.13.2+g2a2fb3b
Kubectl Version: v0.24.2
Jsonnet Version: v0.20.0
argocd app list
NAME CLUSTER NAMESPACE PROJECT STATUS HEALTH SYNCPOLICY CONDITIONS REPO PATH TARGET
argocd/guestbook https://kubernetes.default.svc guestbook default Unknown Healthy <none> <none> https://github.com/argoproj/argocd-example-apps kustomize-guestbook HEAD
argocd/test-openresty https://kubernetes.default.svc test default Synced Healthy Auto <none> http://git/argocdtest/test-openresty.git . develop
argocd/test-pod-sts https://kubernetes.default.svc test default Synced Healthy Auto-Prune <none> http://git/argocdtest/test-pod-sts.git . develop
argocd repo list
TYPE NAME REPO INSECURE OCI LFS CREDS STATUS MESSAGE PROJECT
git http://git/argocdtest/test-openresty.git false false false true Successful default
git http://git/argocdtest/test-pod-sts.git false false false true Successful default
Prometheus监控
Argo CD 本身暴露了两组 Prometheus 指标
如果开启了 endpoints 这种类型的服务自动发现,那么我们可以在几个指标的 Service 上添加 prometheus.io/scrape: "true" 这样的 annotation:
kubectl edit svc argocd-metrics -n argocd
apiVersion: v1
kind: Service
metadata:
annotations:
prometheus.io/scrape: "true"
kubectl edit svc argocd-server-metrics -n argocd
prometheus.io/scrape: "true"
prometheus.io/port: "8083" # 指定8083端口为指标端口
kubectl edit svc argocd-repo-server -n argocd
prometheus.io/scrape: "true"
prometheus.io/port: "8084" # 指定8084端口为指标端口Argo CD 部署样例
Argo CD 提供了一个官网样例,我们就创建一下这个项目吧
样例github地址: https://github.com/argoproj/argocd-example-apps
样例gitee地址: https://gitee.com/cnych/argocd-example-apps
同步说明: https://argo-cd.readthedocs.io/en/latest/user-guide/sync-options/
修改CoreDNS Hosts配置,添加git地址解析
kubectl get configmaps -n kube-system coredns -oyaml
kubectl edit configmaps -n kube-system coredns -oyaml
修改CoreDNS配置文件,将自定义域名添加到hosts中。
例如将www.example.com指向192.168.1.1,通过CoreDNS解析www.example.com时,会返回192.168.1.1。
例如将c1ggit指向10.100.5.1 ,通过CoreDNS解析c1ggit时,会返回10.100.5.1 。
kubernetes cluster.local in-addr.arpa ip6.arpa {
pods insecure
fallthrough in-addr.arpa ip6.arpa
ttl 30
}
hosts {
10.100.5.1 c1ggit
fallthrough
}
prometheus 0.0.0.0:9153各node上创建git的地址
echo ‘10.100.5.1 c1ggit’ >> /etc/hosts
测试外部git地址
kubectl exec busybox-curl -n default — ping c1ggit
PING c1ggit (10.100.5.1): 56 data bytes
64 bytes from 10.100.5.1: seq=0 ttl=60 time=1.755 ms
64 bytes from 10.100.5.1: seq=1 ttl=60 time=1.057 ms- Application Name: app的名称,填写的是样例项目的名称 guestbook
- Project: 是一种资源,用于组织和管理不同的 Kubernetes 应用(Application,目前先写default)
- SYNC POLICY: 同步策略,有手动和自动,样例项目,我们先选择手动Manual
- AUTO-CREATE NAMESPACE: 这里选自动创建应用部署的k8s的命名空间
- SOURCE: Git 仓库,https://github.com/argoproj/argocd-example-apps 就是样例项目的github仓库地址
- Revision: HEAD 分支名
- Path: kustomize-guestbook 资源文件所在的相对路径,Argo CD目前支持多种 Kubernetes 清单,这里需要选择使用那种资源配置模式就选择哪一个路径下的资源清单manifests.根目录可用.
- Cluster URL: Kubernetes API Server 的访问地址,由于 Argo CD 和下发应用的 Kubernetes 集群是同 一个,因此可以直接使用 https://kubernetes.default.svc 来访问
- Namespace: 应用部署在k8s中的命名空间
- PRUNE RESOURCES可以选择是否删除在git中移除的资源,如某个git版本中创建了一个svc,随后又删除了,如果不勾选该选项,则argocd不会自动删除该svc
- SELF HEAL可以理解为自愈,即检测到定义的资源状态和git中不一致的时候,是否自动同步为一致;如git中定义副本数为10,随后手动扩容至20但并未修改git中的配置文件,勾选这一项则会触发argocd自动将副本数缩减回10
- SKIP SCHEMA VALIDATION跳过语法检查,个人不建议开启
- AUTO-CREATE NAMESPACE可以设置如果对应的namespace不存在的话是否自动创建
- APPLY OUT OF SYNC ONLY类似于增量部署而不是全量部署,仅部署和git版本中不一样的资源,而不是全部重新部署一次,可以降低K8S集群的压力
- REPLACE会将部署的命令从默认的kubectl apply变更为kubectl replace/create,可以解决部分资源修改之后无法直接apply部署的问题,同时也有可能会导致资源的重复创建
- RETRY可以设定部署失败后重试的次数和频率
点击页面上面的create按钮
然后手动同步
测试kubernetes.default.svc网络
kubectl exec -it pod/test-pod-0 -n test -- curl -k https://kubernetes.default.svc
{
"kind": "Status",
"apiVersion": "v1",
"metadata": {},
"status": "Failure",
"message": "forbidden: User \"system:anonymous\" cannot get path \"/\"",
"reason": "Forbidden",
"details": {},
"code": 403
}sync同步后可能拉取镜像失败 Back-off pulling image "gcr.io/heptio-images/ks-guestbook-demo:0.1"
https://github.com/argoproj/argocd-example-apps/tree/master/kustomize-guestbook
推送镜像到私仓
gcr.io/heptio-images/ks-guestbook-demo:0.1
docker pull m.daocloud.io/gcr.io/heptio-images/ks-guestbook-demo:0.1
docker tag m.daocloud.io/gcr.io/heptio-images/ks-guestbook-demo:0.1 repo.k8s.local/gcr.io/heptio-images/ks-guestbook-demo:0.1
docker push repo.k8s.local/gcr.io/heptio-images/ks-guestbook-demo:0.1
## 删除原标记
docker rmi m.daocloud.io/gcr.io/heptio-images/ks-guestbook-demo:0.1在线编辑yaml更新image为repo.k8s.local/gcr.io/heptio-images/ks-guestbook-demo:0.1
注意:当argo重启重新拉取yaml后又会不能拉取镜像。
kubectl get pods -n guestbook
NAME READY STATUS RESTARTS AGE
kustomize-guestbook-ui-6c5b4568dc-s2tbh 1/1 Running 0 16m
kubectl get svc -n guestbook
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kustomize-guestbook-ui ClusterIP 10.96.111.171 <none> 80/TCP 16m改成nodeport
kubectl edit svc kustomize-guestbook-ui -n guestbook
nodePort: 30041
type: NodePort
curl http://192.168.244.7:30041/
curl http://10.96.111.171
<html ng-app="redis">
<head>
<title>Guestbook</title>
<link rel="stylesheet" href="//netdna.bootstrapcdn.com/bootstrap/3.1.1/css/bootstrap.min.css">
<script src="https://ajax.googleapis.com/ajax/libs/angularjs/1.2.12/angular.min.js"></script>
<script src="controllers.js"></script>
<script src="https://cdnjs.cloudflare.com/ajax/libs/angular-ui-bootstrap/0.13.0/ui-bootstrap-tpls.js"></script>
</head>
<body ng-controller="RedisCtrl">
<div style="margin-left:20px;">
<div class="row" style="width: 50%;">
<div class="col-sm-6">
<h2>Guestbook</h2>
</div>
<fieldset class="col-sm-6" style="margin-top:15px">
<div class="col-sm-8">
<input ng-model="query" placeholder="Query here" class="form-control" type="text" name="input"><br>
</div>
<div class="col-sm-4">
<button type="button" class="btn btn-primary" ng-click="controller.onSearch()">Search</button>
</div>
</fieldset>
</div>
<div ng-show="showMain" class="main-ui col-sm-6">
<form>
<fieldset>
<input ng-model="msg" placeholder="Messages" class="form-control" type="text" name="input"><br>
<button type="button" class="btn btn-primary" ng-click="controller.onRedis()">Submit</button>
</fieldset>
</form>
<div>
<div ng-repeat="msg in messages track by $index">
{{msg}}
</div>
</div>
</div>
<div ng-hide="showMain" class="search-results row">
</div>
</div>
</body>
</html>
#使用测试pod用域名访问
kubectl exec -it pod/test-pod-1 -n test -- curl http://kustomize-guestbook-ui.guestbook.svcCI/CD
新建公开群组argocdtest
新建项目->导入项目->从url导入仓库
https://github.com/argoproj/argocd-example-apps
开发人员每天把代码提交到 Gitlab 代码仓库
Jenkins 从 Gitlab 代码仓库中拉取项目源码,进行maven编译并打成 jar 包;然后Dockerfile构建成 Docker 镜像,将镜像推送到 Harbor 私有镜像仓库
将镜像推送到 Harbor 私有镜像仓库
- 使用shell,docker build,docker login,docker tag,docker push
- Jenkins 插件式发布镜像,安装 CloudBees Docker Build and Publish
argocd先在git为每个项目创建yaml布署文件,以后监控yaml变化或镜像来自动部署.
Argo CD 默认情况下每 3 分钟会检测 Git 仓库一次,用于判断应用实际状态是否和 Git 中声明的期望状态一致,如果不一致,状态就转换为 OutOfSync。默认情况下并不会触发更新,除非通过 syncPolicy 配置了自动同步。
gitlab
添加拉取用户argocd
将argocd邀请到argocd组,并赋予Developer权限,确认对该组下项目有拉取权限
argocd拉取git项目
1.创建库
Settings->Repositories-> + connect repo
Choose your connection method:VIA HTTPS
Type:git
Project:default #argocd中的命名空间
Repository URL: http://c1ggit/argocdtest/simplenginx.git
username:
Password:
Force HTTP basic auth:true
如通信成功该项目CONNECTION STATUS为Successful.
2.创建应用
Settings->Repositories-> 点击仓库三个点->Create application
Application Name:simplenginx
Project Name:default #argocd中的命名空间
SYNC POLICY:Manual #Automatic
选中AUTO-CREATE NAMESPACE
Repository URL:http://c1ggit/argocdtest/simplenginx.git
Revision:master #git中对应的Branches分支
Path:. #.当前根目录
Cluster URL:https://kubernetes.default.svc
Namespace:test
3.同步应用
点击SYNC,SYNC STATUS为Synced表示成功
对接LDAP(可选)
ldap-patch-dex.yaml
vi ldap-patch-dex.yaml
# Please edit the object below. Lines beginning with a '#' will be ignored,
# and an empty file will abort the edit. If an error occurs while saving this file will be
# reopened with the relevant failures.
#
apiVersion: v1
data:
dex.config: |-
connectors:
- type: ldap
name: ..................
id: ldap
config:
# Ldap server address
host: 192.168.5.16:389
insecureNoSSL: true
insecureSkipVerify: true
# Variable name stores ldap bindDN in argocd-secret
bindDN: "$dex.ldap.bindDN"
# Variable name stores ldap bind password in argocd-secret
bindPW: "$dex.ldap.bindPW"
usernamePrompt: .........
# Ldap user serch attributes
userSearch:
baseDN: "ou=people,dc=xxx,dc=com"
filter: "(objectClass=person)"
username: uid
idAttr: uid
emailAttr: mail
nameAttr: cn
# Ldap group serch attributes
groupSearch:
baseDN: "ou=argocd,ou=group,dc=xxx,dc=com"
filter: "(objectClass=groupOfUniqueNames)"
userAttr: DN
groupAttr: uniqueMember
nameAttr: cn
# 注意:这个是argocd的访问地址,必须配置,否则会导致不会跳转.
url: https://192.168.80.180:30984configMap
kubectl -n argocd patch configmaps argocd-cm --patch "$(cat ldap-patch-dex.yaml)"
kubectl edit cm argocd-cm -n argocdsecret
# bindDN是cn=admin,dc=xxx,dc=com
kubectl -n argocd patch secrets argocd-secret --patch "{\"data\":{\"dex.ldap.bindDN\":\"$(echo cn=admin,dc=xxx,dc=com | base64 -w 0)\"}}"
# 密码bindPW是123456
kubectl -n argocd patch secrets argocd-secret --patch "{\"data\":{\"dex.ldap.bindPW\":\"$(echo 123456 | base64 -w 0)\"}}"删除POD,以重启,让上面的ldap配置生效。
Argo CD Image Updater
wget https://raw.githubusercontent.com/argoproj-labs/argocd-image-updater/stable/manifests/install.yaml -O argocd-image-updater.yaml
cat argocd-image-updater.yaml|grep image:
image: quay.io/argoprojlabs/argocd-image-updater:v0.12.0本地私仓镜像
docker pull quay.io/argoprojlabs/argocd-image-updater:v0.12.0
docker tag quay.io/argoprojlabs/argocd-image-updater:v0.12.0 repo.k8s.local/quay.io/argoprojlabs/argocd-image-updater:v0.12.0
docker push repo.k8s.local/quay.io/argoprojlabs/argocd-image-updater:v0.12.0
docker rmi quay.io/argoprojlabs/argocd-image-updater:v0.12.0#测试
sed -n "/image:/{s/image: /image: repo.k8s.local\//p}" argocd-image-updater.yaml
#替换
sed -i "/image:/{s/image: /image: repo.k8s.local\//}" argocd-image-updater.yamlkubectl apply -n argocd -f argocd-image-updater.yaml
serviceaccount/argocd-image-updater created
role.rbac.authorization.k8s.io/argocd-image-updater created
rolebinding.rbac.authorization.k8s.io/argocd-image-updater created
configmap/argocd-image-updater-config created
configmap/argocd-image-updater-ssh-config created
secret/argocd-image-updater-secret created
deployment.apps/argocd-image-updater createdArgoCD 中的用户和角色
管理员CLI 登录
输入的Ip地址就是argocd-server的ClusterIP 可以通过命令查询
kubectl get svc -n argocd
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
argocd-applicationset-controller ClusterIP 10.96.248.76 <none> 7000/TCP,8080/TCP 25d
argocd-dex-server ClusterIP 10.96.159.94 <none> 5556/TCP,5557/TCP,5558/TCP 25d
argocd-metrics ClusterIP 10.96.31.187 <none> 8082/TCP 25d
argocd-notifications-controller-metrics ClusterIP 10.96.199.238 <none> 9001/TCP 25d
argocd-redis ClusterIP 10.96.94.14 <none> 6379/TCP 25d
argocd-repo-server ClusterIP 10.96.255.97 <none> 8081/TCP,8084/TCP 25d
argocd-server ClusterIP 10.96.10.228 <none> 80/TCP,443/TCP 25d
argocd-server-metrics ClusterIP 10.96.117.128 <none> 8083/TCP 25dargocd login argocd-server.argocd.svc.cluster.local
kubectl get svc -n argocd |grep argocd-server|head -n1 |awk ‘{print $3}’
argocd login 10.96.10.228
WARNING: server certificate had error: tls: failed to verify certificate: x509: cannot validate certificate for 10.96.10.228 because it doesn't contain any IP SANs. Proceed insecurely (y/n)? y
Username: admin
Password:
'admin:login' logged in successfully
Context '10.96.10.228' updated一句话登录
echo y | argocd login $(kubectl get svc -n argocd |grep argocd-server|head -n1 |awk ‘{print $3}’)–password ‘c1gstudio’ –username admin
登出:
#argocd logout argocd-server.argocd.svc.cluster.local
argocd logout 10.96.10.228添加 用户
在 argocd/argocd-cm
添加gitops 用户,有生成 apiKey 和 login 权限。
添加system用户代替admin,后继关闭admin用户
添加测试用户dev_user
添加发布用户pre_user
kubectl edit cm argocd-cm -n argocd
apiVersion: v1
data:
accounts.gitops: apiKey, login
accounts.system.enabled: "true"
accounts.dev_user: login
accounts.system.enabled: "true"
accounts.pre_user: login
accounts.system.enabled: "true"
accounts.system: login
accounts.system.enabled: "true"
admin.enabled: "true"
kind: ConfigMap修改后,会热加载,无需重启任何服务。
用 admin 用户登录后,修改 gitops 的密码为 gitops@smallsoup(注意 current-password 是当前登录用户的密码,如果用 admin 登录的,就是 admin 的密码)
查账号
argocd account get –account gitops
列出账号
argocd account list
NAME ENABLED CAPABILITIES
admin true login
dev_user true login
gitops true login
pre_user true login
system true login更新用户密码
argocd account update-password \
--account gitops \
--current-password 'c1gstudio' \
--new-password 'gitopsPass123'
argocd account update-password \
--account system \
--current-password 'c1gstudio' \
--new-password 'Pass123456'
argocd account update-password \
--account dev_user \
--current-password 'c1gstudio' \
--new-password 'Pass123456'
argocd account update-password \
--account pre_user \
--current-password 'c1gstudio' \
--new-password 'Pass123456'测试登录
echo y | argocd login $(kubectl get svc -n argocd |grep argocd-server|head -n1 |awk ‘{print $3}’) –password ‘gitopsPass123’ –username gitops
目前还没有权限查看资源
argocd account list
argocd cluster list
argocd app list
生成Token (这样生成的 token 从不过期,可以加–expires-in 参数设置过期时长)
argocd account generate-token –account gitops
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhcmdvY2QiLCJzdWIiOiJnaXRvcHM6YXBpS2V5IiwibmJmIjoxNzAyODgzMDEwLCJpYXQiOjE3MDI4ODMwMTAsImp0aSI6IjM3M2U0NTRhLTlkMjktNGU4My04ZTgyLWIwNWE1MWMyZjVhNiJ9.esoLwNwxBGp1MXt6-eFBSL-4lbI9_a-CRgk6NZrQyG4
#使用Token查看
argocd app list --auth-token eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJhcmdvY2QiLCJzdWIiOiJnaXRvcHM6YXBpS2V5IiwibmJmIjoxNzAyODgzMDEwLCJpYXQiOjE3MDI4ODMwMTAsImp0aSI6IjM3M2U0NTRhLTlkMjktNGU4My04ZTgyLWIwNWE1MWMyZjVhNiJ9.esoLwNwxBGp1MXt6-eFBSL-4lbI9_a-CRgk6NZrQyG4 --server $(kubectl get svc -n argocd |grep argocd-server|head -n1 |awk '{print $3}' --insecure权限
Kubernetes Argo CD权限提升漏洞
2.3.3之前版本
kubectl get -n argocd cm argocd-cm -o jsonpath=’{.data.users.anonymous.enabled}’
如果此命令的结果为空或 "false",则表示未启用对该实例的匿名访问。如果结果是 "true",则意味着实例很容易受到攻击。
默认用户组
内置两条用户组 ,只读用户组和管理员用户组
role:readonly – read-only access to all resources
role:admin – unrestricted access to all resources
禁用 匿名访问
kubectl patch -n argocd cm argocd-cm –type=json -p='[{"op":"add","path":"/data/users.anonymous.enabled","value":"false"}]’
权限格式
p, <role/user/group>, <resource>, <action>, <object>
p, <role/user/group>, <resource>, <action>, <appproject>/<object>资源和动作有下面这些:
Resources: clusters, projects, applications, applicationsets, repositories, certificates, accounts, gpgkeys, logs, exec ,extensions
Actions: get, create, update, delete, sync, override, action/<group/kind/action-name>sync, override, and action/<group/kind/action-name> 仅对 applications 有效
给权限
给system管理员权限
gitops给gitops组权限
pre_user给qagroup组权限,不能创建projects
test_user都可以看,但只能操作localtest项目权限,相当于命名空间隔离。
test_user可以对default项目中的simplenginx应用,执行同步操作。
dev_user只能操作dev-开头的项目
默认只读
policy.default: role:readonly
在 argocd-rbac-cm Configmaps 中给增加以下 policy.csv 就可以看到 admin 创建的 app、仓库等信息了:
kubectl edit cm argocd-rbac-cm -n argocd
data:
policy.default: role:readonly
policy.csv: |
p, role:gitops, applications, get, *, allow
p, role:gitops, applications, create, *, allow
p, role:gitops, applications, update, *, allow
p, role:gitops, applications, sync, *, allow
p, role:gitops, applications, override, *, allow
p, role:gitops, applications, delete, *, allow
p, role:gitops, applications, action/argoproj.io/Rollout/*, *, allow
p, role:gitops, repositories, get, *, allow
p, role:gitops, repositories, create, *, allow
p, role:gitops, repositories, update, *, allow
p, role:gitops, projects, create, *, allow
p, role:gitops, projects, get, *, allow
p, role:gitops, clusters, get, *, allow
p, role:gitops, clusters, list, *, allow
p, role:gitops, exec, create, */*, allow
p, role:qagroup, applications, get, *, allow
p, role:qagroup, applications, create, *, allow
p, role:qagroup, applications, update, *, allow
p, role:qagroup, applications, sync, *, allow
p, role:qagroup, applications, override, *, allow
p, role:qagroup, applications, delete, *, allow
p, role:qagroup, applications, action/argoproj.io/Rollout/*, *, allow
p, role:qagroup, repositories, get, *, allow
p, role:qagroup, repositories, create, *, allow
p, role:qagroup, repositories, update, *, allow
p, role:qagroup, projects, get, *, allow
p, role:qagroup, clusters, get, *, allow
p, role:qagroup, clusters, list, *, allow
p, role:qagroup, exec, create, *, allow
p, role:devgroup, applications, get, dev-*/*, allow
p, role:devgroup, applications, create, dev-*/*, allow
p, role:devgroup, applications, update, dev-*/*, allow
p, role:devgroup, applications, sync, dev-*/*, allow
p, role:devgroup, applications, override, dev-*/*, allow
p, role:devgroup, applications, delete, dev-*/*, allow
p, role:devgroup, applications, action/argoproj.io/Rollout/*, *, allow
p, role:devgroup, repositories, get, dev-*/*, allow
p, role:devgroup, repositories, create, dev-*/*, allow
p, role:devgroup, repositories, update, dev-*/*, allow
p, role:devgroup, projects, get, dev-*/*, allow
p, role:devgroup, clusters, get, dev-*/*, allow
p, role:devgroup, clusters, list, dev-*/*, allow
p, role:devgroup, exec, create, dev-*/*, allow
p, test_user, *, *, localtest/*, allow
p, test_user, applications, create, default/simplenginx, deny
p, test_user, applications, update, default/simplenginx, allow
p, test_user, applications, sync, default/simplenginx, allow
p, test_user, applications, delete, default/simplenginx, allow
p, test_user, applications, override, default/simplenginx, allow
g, pre_user, role:qagroup
g, dev_user, role:devgroup
g, gitops, role:gitops
g, system, role:admin
apiVersion: v1
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/name: argocd-rbac-cm
app.kubernetes.io/part-of: argocd
name: argocd-rbac-cm
namespace: argocd参考文档:
用户管理:https://argoproj.github.io/argo-cd/operator-manual/user-management/
RBAC控制:https://argoproj.github.io/argo-cd/operator-manual/rbac/
https://argo-cd.readthedocs.io/en/stable/operator-manual/rbac/
禁用 admin
方式一
kubectl patch -n argocd cm argocd-cm --type=json -p='[{"op":"replace","path":"/data/admin.enabled","value":"false"}]'方式二
kubectl edit cm argocd-cm -n argocd
admin.enabled: "false"删除用户
kubectl patch -n argocd cm argocd-cm –type=’json’ -p='[{"op": "remove", "path": "/data/accounts.dev_user"}]’
kubectl patch -n argocd secrets argocd-secret –type=’json’ -p='[{"op": "remove", "path": "/data/accounts.dev_user.password"}]’
Web-based Terminal 终端功能
参考:https://argo-cd.readthedocs.io/en/stable/operator-manual/web_based_terminal/
从 Argo CD v2.4起,默认情况下会禁用此功能,它允许用户在他们拥有exec/create权限的应用程序管理的任何Pod上运行任意代码。
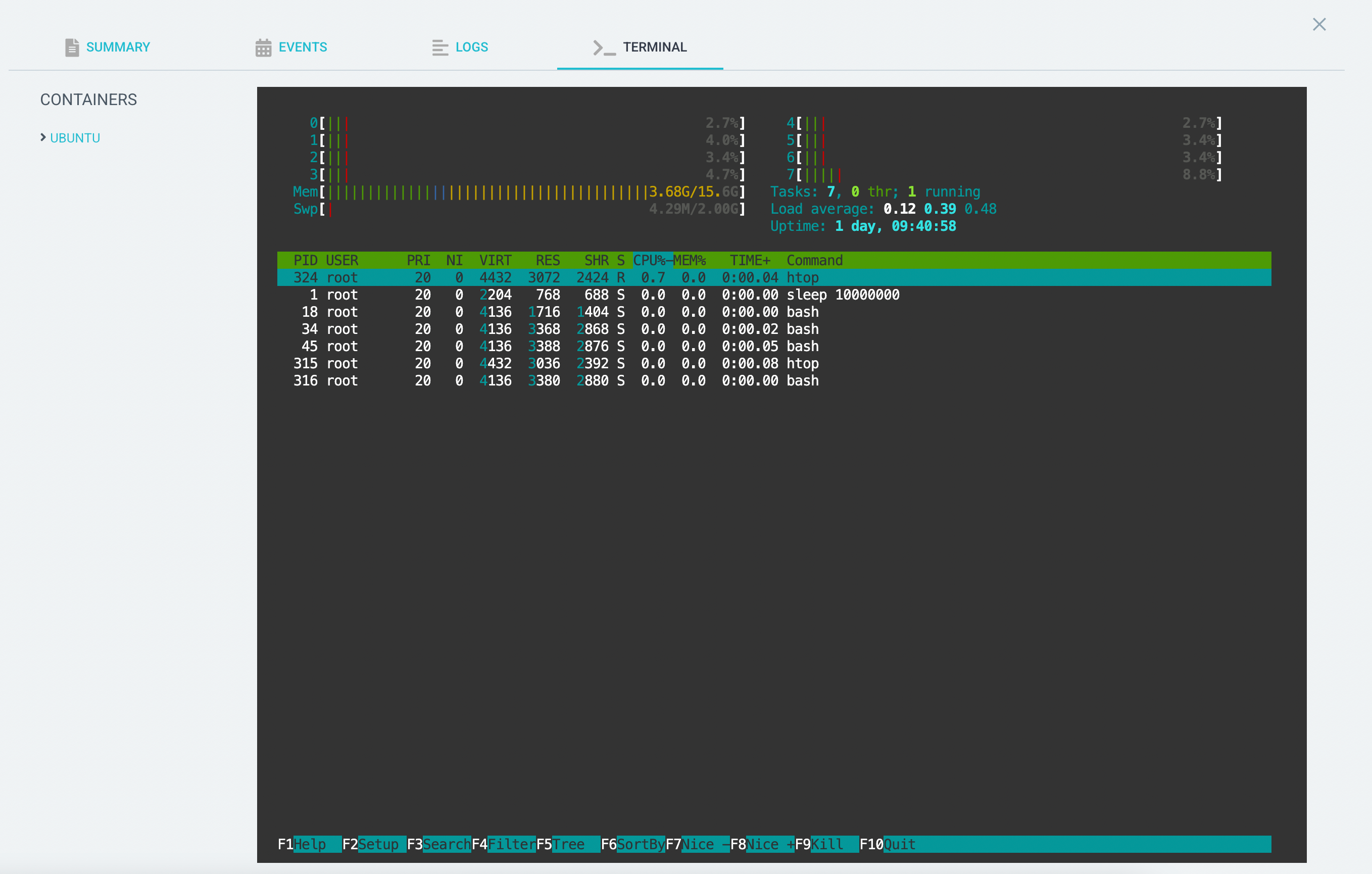
1.打开exec功能
kubectl edit cm argocd-cm -n argocd
data:
exec.enabled: "true"2.添加权限
添加到尾部
kubectl get clusterrole argocd-server
kubectl edit clusterrole argocd-server
- apiGroups:
- ""
resources:
- pods/exec
verbs:
- create3.添加RBAC权限
在相应组下添加权限
kubectl edit cm argocd-rbac-cm -n argocd
p, role:myrole, exec, create, */*, allow

No Responses (yet)
Stay in touch with the conversation, subscribe to the RSS feed for comments on this post.